When IT Goes Wrong
It’s Not Just Cybersecurity That Costs You

When IT Goes Wrong: It’s Not Just Cybersecurity That Costs You
High-profile cyber attacks have dominated headlines in recent weeks, with Marks & Spencer and the Co-op both suffering major disruptions to their operations and customer services. Luxury retailer Harrods was also hit by a cyber incident, requiring system shutdowns to contain the threat. These incidents, which all occurred within days of each other, have exposed serious vulnerabilities across the UK retail sector Which prompted the National Cyber Security Centre to issue a warning that no business is immune.
While these are big names are making the news, the reality is that cyber threats and the true costs of IT underinvestment can impact organisations of any size.
Learning from Others: Are You Prepared?
An insider reportedly claimed one major retailer “didn’t have a cyber attack plan in place” during their breach. While this hasn’t been officially confirmed, it raises an important question for every business: is your organisation truly prepared for IT challenges?
It’s not a matter of if you’ll face IT issues, but when. How you respond makes all the difference.
The Real Costs of IT Failures
When IT goes wrong, the consequences go far beyond lost data or money. It can affect your business in multiple ways:
• Financial Penalties: Regulatory fines for mishandling personal data can reach millions under GDPR and other laws.
• Reputation Damage: Customers lose trust when their information is exposed, and that trust can take years to rebuild.
• Operational Disruption: Even minor technical issues can halt business operations, leading to lost revenue and frustrated staff.
• Legal Risks: Beyond fines, poor IT practices can expose your business to legal action and compliance failures.
• Hidden Costs: Outdated systems and lack of staff training gradually erode productivity and inflate operating costs.
Why IT is More Than Cybersecurity
Cybersecurity is a crucial part of your IT strategy, but it’s only one part of effective Risk IT management. Other risks can cause just as much damage if overlooked:
• Business Continuity: Do you have a tested plan to keep things running if systems go down?
• Access Control: Are permissions managed properly to minimise errors and prevent unauthorised access?
• Third-Party Risks: Are your suppliers secure, or could their vulnerabilities affect you?
• Software Licensing: Are your licences current and compliant, or are you risking surprise costs or outages?
• Staff Readiness: Does your team know what to do when IT issues strike?
Shifting from Reacting to Planning: Working Smarter with IT
Often businesses fall into a cycle of reacting to urgent IT problems like outages, security incidents, or failed backups, putting out one fire after another. These tasks are urgent and important, but they often consume valuable time, resources and energy that could be used more strategically.
True resilience is built by focusing on proactive, forward-thinking, for example; risk assessments, system audits, team training, and long-term planning. These are the investments that help prevent emergencies before they happen and support business growth over time.
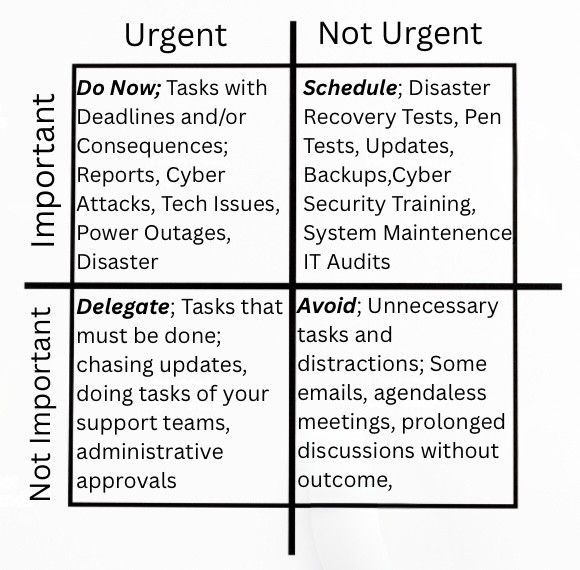
The Eisenhower Matrix is a well-known time management tool categorises these efforts as “important but not urgent.” Prioritising this kind of work not only protects your organisation, but also frees up time to focus on innovation and improvement.
Quadrant 1 tasks in the Eisenhower Matrix: urgent and important, demanding immediate attention to keep the business running.
Quadrant 2 tasks in the Eisenhower Matrix: important but not urgent tasks, building solid systems and processes, businesses can reduce stress, optimise resources, and stay ahead of potential risks.
Below is an Example of Stephen R. Covey’s Time Management Matrix, 7 Habits of Highly Effective People.
Transparency and Trust: Lessons from the Headlines
Both Marks & Spencer and the Co-op issued public statements and updates following the attacks, providing transparency and acknowledging the impact on their customers. While some details particularly around the extent of customer data exposure remain unclear, their openness helped towards managing customer concerns and demonstrated a willingness to take responsibility.
Though the fallout continues. Marks & Spencer’s shares initially fell by almost 7%, losing upwards of £650 million from the company’s value in a matter of days, their shares fell yet again 4.7% yesterday, it's losses since this major cyber attack have now reached more than £1billion. It is estimated Marks & Spencer is potentially losing over £3 million a day while their online platform remains closed for purchases.
In the case of the Co-op, customer data was reportedly compromised. The consequences of this are more than technical issues and financial losses from potential fines, this is where customer’s trust in the brand is put to the test. A breach of this nature risks long-term reputational damage, especially in a time when consumer expectations for data security are higher than ever.
A recent survey found that 66% of consumers lose trust in a company following a data breach, and 70% would stop doing business with a brand after a serious security incident. This reflects customer loyalty as a main concern.
Reflection for Businesses
Take a moment to consider:
• If your business faced a major IT disruption, how confident are you that your team could respond quickly and effectively?
• If your customers understood your approach to cybersecurity and IT planning, would they feel confident in the protection of their data?
Final Thoughts: Is Your IT Strategy Ready for Tomorrow?
Proactive IT management while it is about avoiding disasters, it’s also about helping your business operate efficiently, meet regulatory obligations, and build trust with your customers.
By creating strong collaboration between leadership, your CTO (whether full-time or fractional), and your IT team (internal or external) you lay the foundation for resilience and sustainable growth.
Now more than ever, the question is not can you afford to invest in strategic IT management, but can you afford not to.
References and further reading.
FoodNavigator: M&S, Co-op, Harrods cyber attacks
Infosecurity Magazine: DragonForce group tied to attacks
Reuters: M&S, Co-op, Harrods breaches
Computing: Harrods latest target
BBC News: Harrods cyber attack
Cloud & More: What M&S, Harrods, and Co-op teach us
BBC News: Beware phony IT calls after hacks
Sky News: M&S ‘had no plan’ for cyber attacks